An npm audit reports almost 300 vulnerabilities on a newly created SharePoint Framework project. What are the odds that because of the sheer number, developers ignored the warnings altogether and provided you with a solution that exposes your organization to security risks?
A new model for extending SharePoint
SharePoint Framework is a new model for building SharePoint applications. Unlike other SharePoint development models available to-date, SharePoint Framework uses open-source toolchain based on Node.js. Applications built using the SharePoint Framework consist 100% of JavaScript that runs in the web browser.
Honeypot
Because of their rising popularity, Node.js and its 800.000 packages are regularly a target for hackers who try to exploit the vulnerabilities and gain access to sensitive information. To raise awareness, npm – the Node.js package manager, recently started automatically auditing solutions and reporting vulnerabilities in the used packages. But in the context of the SharePoint Framework it kind of backfires.
300 vulnerabilities?
An npm audit executed on a newly created SharePoint Framework reports almost 300 vulnerabilities, over 150 of which are high severity. This is enough to paralyze developers and have them look the other way.
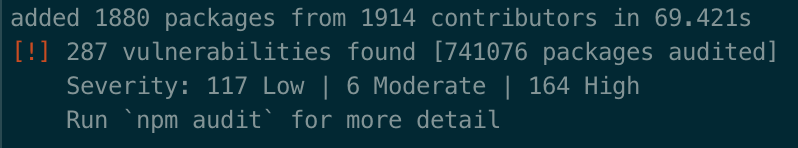
Many of these vulnerabilities apply to packages that are a part of the SharePoint Framework toolchain and have nothing to do with the code that ends up in production. But because developers don’t bother to review the 300 vulnerabilities, they wouldn’t even know if they’re shipping something malicious or not.
Trust but verify
Some developers are more thorough when it comes to security than others. You should trust your developers, but you should also verify their work. And it’s not trivial because what you get is a zip package, which you need to open, go through the code files to discover dependencies, and find out the version of each one and then see if there are any vulnerabilities reported in that particular version. It’s tedious to say the least. Luckily, there are tools that simplify this process a lot.
Using the Rencore platform, you can easily see if the solution contains any known vulnerabilities or not and if so, what they are and how they can be mitigated. If you’re analyzing packaged solutions, like SharePoint Framework applications, you can use Rencore as a part of your deployment process and run the analysis fully automated.
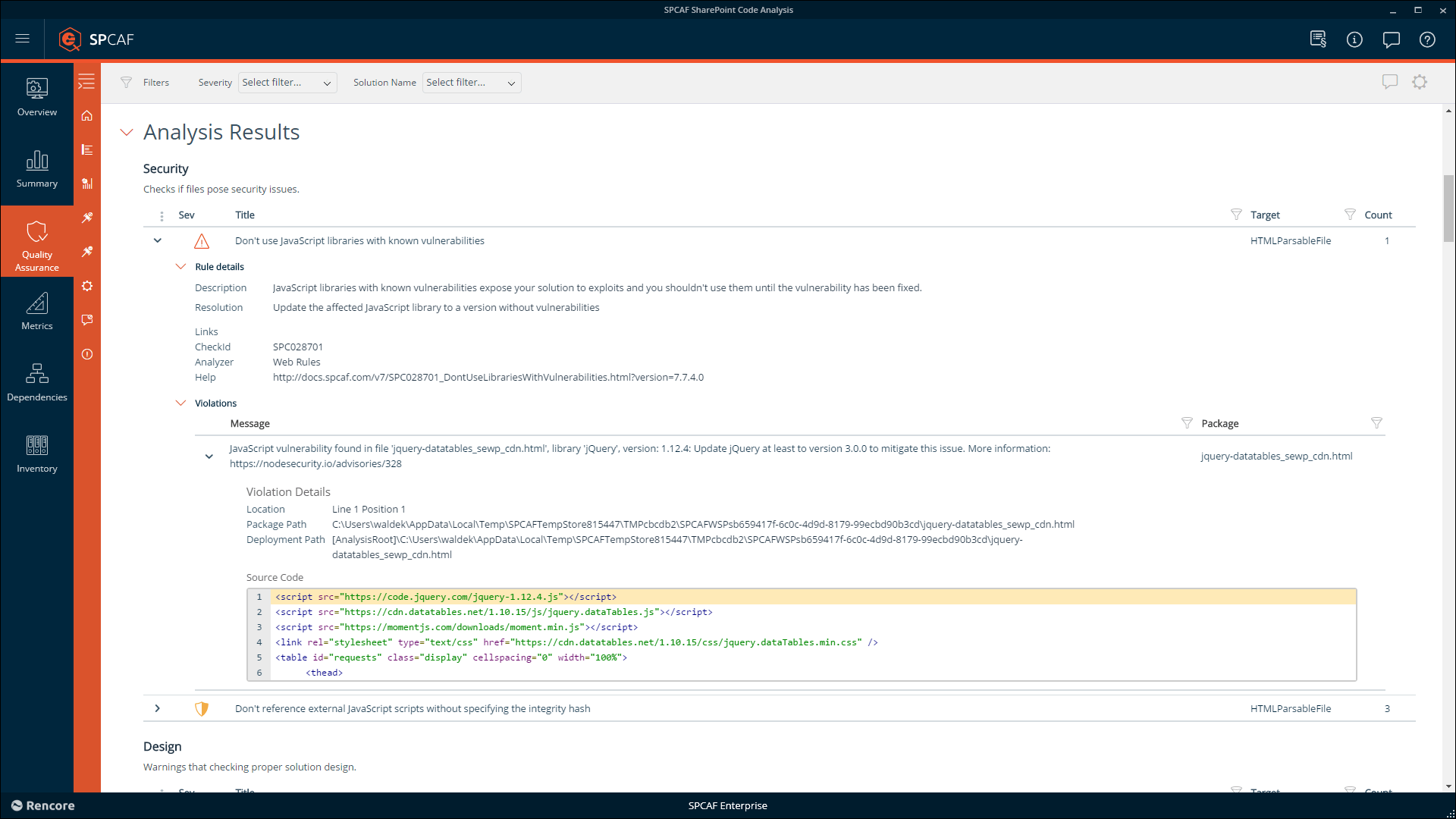
But packaged solutions are not the only source of vulnerabilities. End-users adding JavaScript widgets from the Internet to SharePoint pages can also expose your organization to security risks. By continuously monitoring your SharePoint environment, the Rencore platform helps you discover these end-user applications and verify if they pose any threats to your organization.
New vulnerabilities are discovered every day, which is why it’s not enough to audit your SharePoint applications and environment only once. Even if you don’t change your code or its dependencies, regularly analyzing your applications will help you discover any threats before they become an issue. Rencore simplifies it, allowing you to focus on helping your organization to stay secure.
SharePoint Framework Whitepaper
Authored by Microsoft MVPs Waldek Mastykarz and Erwin van Hunen, this free whitepaper provides a comprehensive guide on how administrators can deal with SharePoint Framework to maximize the security of SharePoint and Office 365 environments.




