This is part 5, and the last part of a longer series in securing SharePoint Online as part of securing Office 365. The purpose in writing this is to provide a more comprehensive look into the aspects of SharePoint Online security, especially for those who might not have extensive experience in working with SharePoint Online yet.
The whole series contains the following articles:
- SharePoint Online and security: Overview
- Securing users and admins
- Securing content in SharePoint Online
- SharePoint Online external sharing and extranets
- Advanced security with Azure Active Directory (this article)
About Azure Active Directory and security
Azure Active Directory is at the core of everything in Office 365 and Microsoft Azure. While it’s responsible for securing and providing identities for users, it also manages many other settings and services – including several security-related services we will need when securing SharePoint Online.
As Azure AD comes in both free and paid licenses (per user), it’s often a requirement to purchase the premium licenses for certain features. These can be purchased separately but a more financially sound approach is to buy them in bulk with a license package such as Enterprise Mobility + Security (EMS) E3 or E5 offering. Of course, there are other bundles as well, such as Microsoft 365 E3/E5.
What Azure AD Premium P1/P2 license grants in terms of security include
- Advanced security reports (P1, P2)
- Group-based access management (P1, P2)
- Self-service password reset, change and unlock for users (P1, P2)
- Multi-Factor Authentication (MFA) (P1, P2)
- Cloud App Discovery (P1, P2)
- Connect Health (P1, P2)
- Conditional access (P1, P2)
- Identity Protection (P2 only)
Privileged Identity Management (P2 only)
You can view all features, including non-security related here. You’ll note there’s a Basic license available as well. I’m not commonly seeing this, as many organizations go direct to P1 or P2 from the free license.
It’s not required to enable and configure all these features to be secure. As you might realize many services are for securing identities and access, and therefore provide additional security for SharePoint Online.
So many to choose from – so start with these
As I noted in part 2 of this series, multi-factor authentication is crucial. Start with that to secure your users and admins. With Azure AD Premium P1 (and P2, as it includes all P1 capabilities while adding a few others listed above) you can also do conditional access.
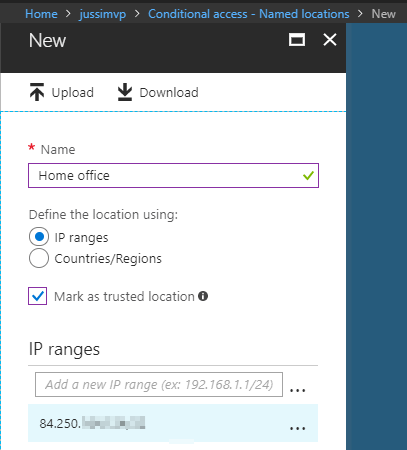
With conditional access, we can dynamically enforce additional rules and requirements for users during their login attempts. As an example, I’ll first create a trusted location for conditional access through the Azure AD blade in Azure Portal. If you get tired of finding the correct place, there’s a nice subset for AAD settings under https://aad.portal.azure.com.
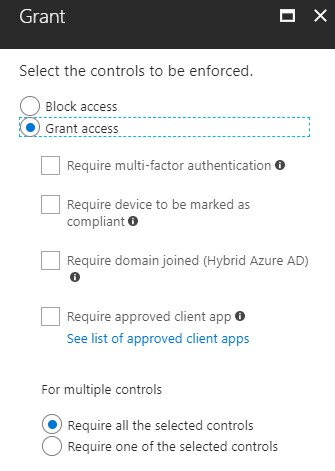
With the trusted location I can specify IP ranges, including just a single IP address, or countries and regions. The purpose for setting a country would be a sort of “block everyone outside my country” approach. While not bulletproof, it provides an easy way to block out most suspicious login attempts. With this trusted location I can now build one or more policies that enforce additional security settings. These could include enforced MFA, forced password reset or requiring the device the user is using to be compliant.
We can also finetune this policy to only apply to certain users, location and specific apps. Consider a scenario where the user needs to access highly sensitive content stored in SharePoint Online in a specific site collection. We could block all access for users unless they access the sensitive content through a trusted location (a specific country, or an IP address), or perhaps using a specific device or app.
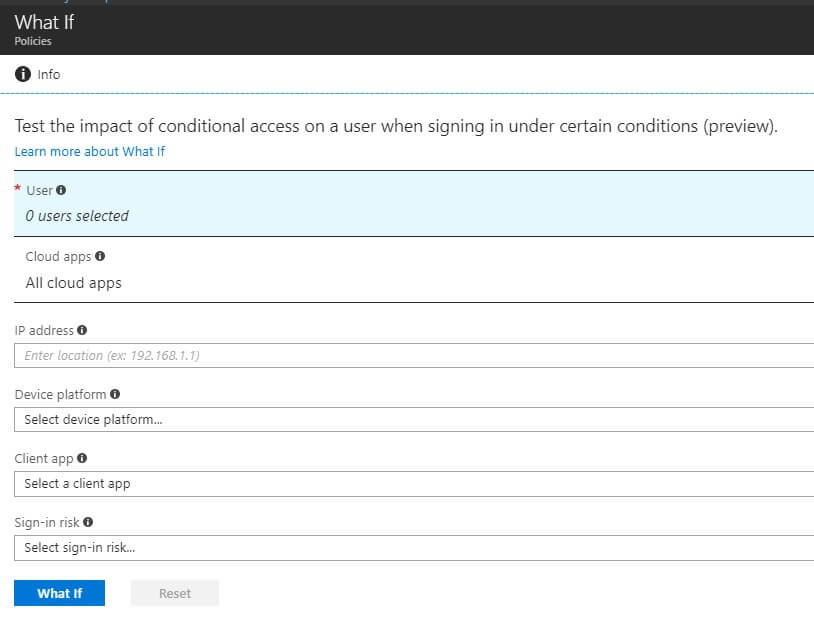
While configuring conditional access start with the easy policies as there’s a risk of accidentally locking yourself out. That’s why there’s a “what if”-tool for testing when and how policies are interpreted.
In my experience conditional access is often not configured, even if the license would permit the additional security it provides. At a minimum level organizations should enforce MFA if users are logging outside trusted (named) locations.
I’m lost, why isn’t SharePoint Online secure by default?
Many times, organizations and especially their IT admins wonder why there is a need for so many security services, settings and capabilities within Azure, Azure AD and Office 365. Isn’t SharePoint Online secure by default?
For many customers, I’ve seen over the years, SharePoint Online is secure. Only in the past year or so I’ve been seeing a growing demand for encrypted email, additional access privileges and deeper reporting demands. Microsoft is answering this demand especially with the E5 (EMS, O365, M365) capabilities. While one could argue it would be nice to have these as part of existing E1 and E3 licenses, I understand many features are specific enough to only attract customers who are ready to invest in their security practices a bit more.
Always start with the built-in features your license includes and consider moving up the ladder when a real need or requirement arises. Sometimes it’s also possible to build a custom solution, which might prove more worthwhile if the need is only for a single functionality that might not be available separately.
Certain features, such as Compliance Manager, however are included in most Office 365 license plans. With the latest announcement, Compliance Manager is also generally available and now reaches Azure, Office 365 and Dynamics services.
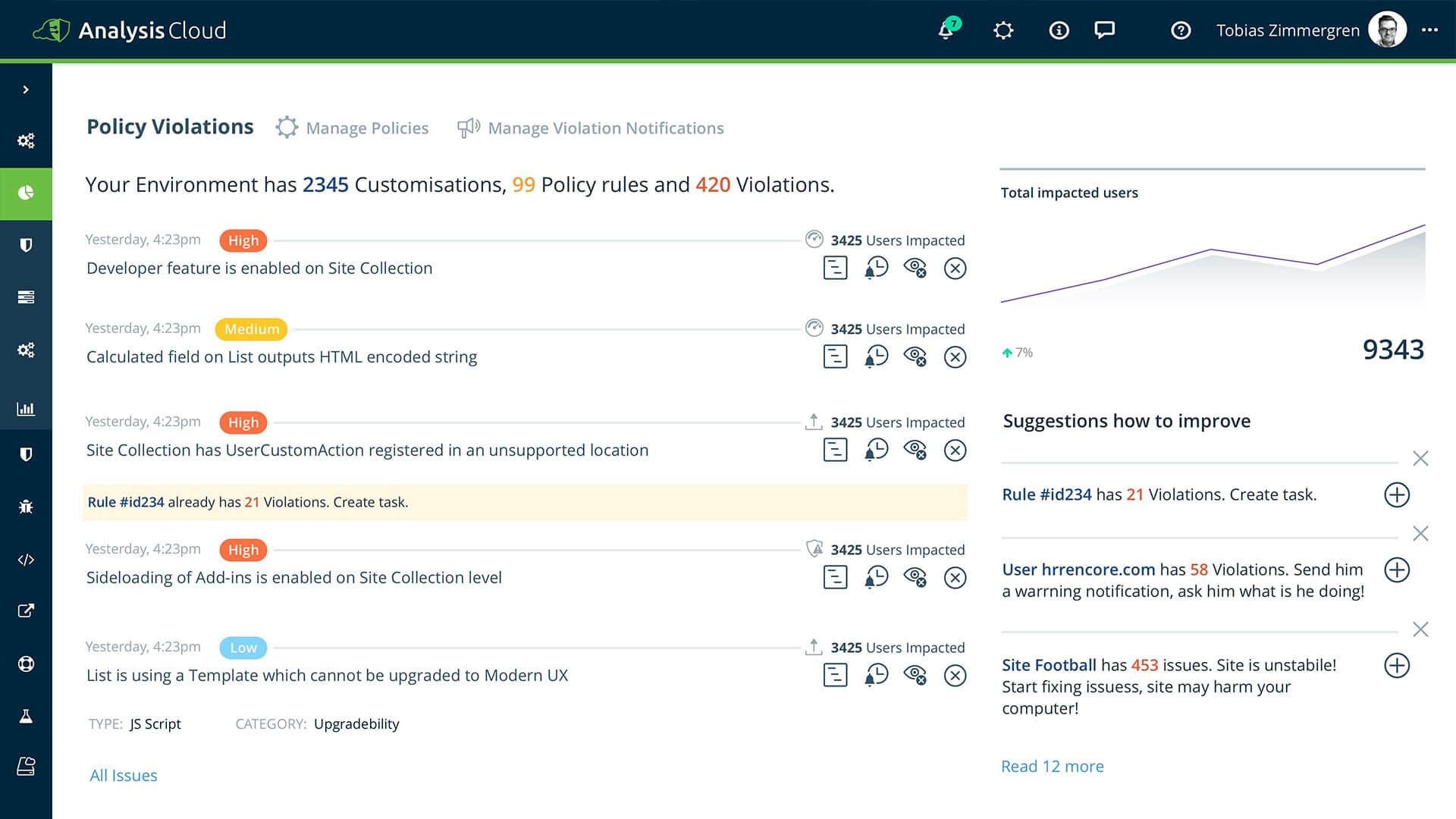
In addition, certain elements of securing SharePoint Online might not come from Microsoft. I want to highlight one large area that organizations might often miss: customizations admins and users might deploy to their SharePoint Online sites. While access to SharePoint Online might be efficiently secured, what users are doing within the service is another matter. For this, the Rencore AnalysisCloud provides governance and visibility.
Best practices
As we’ve seen many times during this series in the past weeks, the best practice for securing SharePoint Online is about understanding your needs. Add to this the capabilities your current licensing models allow, figure out what you might be missing and make sure to start small. If you pile up all services, settings and requirements at once you might – or might not – be super secure, but your users might be very vocal about the changes.
Remember to verify your secure score regularly and make the appropriate planning and changes over time.
In closing
It’s been a joy and pleasure to highlight the possibilities on how to secure SharePoint Online in this series. Best of luck in your journey towards securing SharePoint Online. Follow Rencore and myself on Twitter for regular news, updates and thoughts on these topics!
Over to you
Why not check out the Security in and with Office 365 using Secure Code eBook by Jethro Seghers. This eBook is solely dedicated to explaining and helping you improve the Security in and with Office 365. Download this eBook for free today!