In the past, creating applications, business processes or merely enhancing the user interface of an existing application required a developer. Changes such as these had to be completed using code that ran within the core application itself, making it near impossible for anyone else to make the changes. As Cloud Services have risen in popularity, vendors have re-built their on-premises applications into web-based solutions that are available from any device, at any time from anywhere.
Organizations are pushing cloud vendors to allow customizations to be made quickly without the need for developers. There is an advantage to this for both the vendor and the customer. Providing a platform that can be easily customized to fit a business need without requiring managed code allows vendors to dictate the level and types of changes allowed. Most cloud providers have chosen the industry standard approach of allowing custom styling using Cascading Style Sheets (CSS), injection of JavaScript and modification of Hypertext Markup Language (HTML), as well as providing data modification using objects such as JavaScript Object Notation (JSON).
Click the button below and find out about Advanced Security Management tools.
These new streamlined online application platforms that are now available today make it easier than ever to create low or no-code solutions. This type of development is not for the core software developer, but aimed at a new category of developers called “Citizen Developer.”
What are Citizen Developers?
Citizen Developers are business users who create application enhancements that facilitate a business process while following the development guidelines of IT. They may not have any formal development training in programming, and creating solutions is probably not part of their actual job description. They have creative ideas for improving areas of the business such as customer relationship management, internal operations, and product development. You probably recognize the citizen developers all around you already. They are the ones that already experiment with various configurations of Excel spreadsheets or even Access databases to improve current processes. Citizen development can bring a positive impact to any business by:
- Quickly bringing new capabilities and apps online
- Empowering knowledge workers to build technical workarounds to problems
- Increasing organizational speed, agility, and deployment
- Removing the reliance and pressure off an already busy IT Department
Citizen development also complicates matters.
Is there a risk attached to Citizen Developers?
There are real threats in allowing novice programmers, with no formal training and certifications to hack solutions together. Generally “hacking” it together, means to take existing public code, found via an internet search, and us it without really understanding what it does or does not do. When this is the case, the organization can be open to data and security attacks, as well as exposing vulnerabilities within the new applications.
In a recent webinar provided by Rencore’s very own Waldek Mastykarz, an example came up where JavaScript code was running within Microsoft’s Office 365 service, and upon executing, rendered to an end-user a prompt to contact the helpdesk with a crafted message stating “ Please contact your Administrator.” Upon the Administrator accessing the same page containing the JavaScript, the code authenticated as them and retrieved content such as documents owned by them and sent them externally outside of the organization. The citizen developer did not set out to break the application or perform any malicious actions. It was not a hack; it was not a security breach, the code was allowed to be added to the platform and was sanctioned by IT.
Alan Lepofsky, VP and Principal Analyst at Constellation Research states the following:
Traditionally, knowledge workers had to rely on their IT department to develop and deploy applications. It can often be a lengthy and expensive process. But now the rise of low-code and even no-code solutions, which enable ‘non-developers’ to use drag-and-drop to add fields, buttons, and basic programming logic to forms is enabling people to create applications to assist in their business processes.
Lepofsky further states:
While these new solutions are easy to create, a level of control is still required, so that areas like corporate branding, compliance, and governance aren’t overlooked.
Allowing Citizen Developers unfettered access to sensitive data, or full access to make any changes they deem essential raises many security risks. Four key risks need addressing:
Greater chance of Data and Security Breaches
Although cloud services provide security features, these focus on Authentication, Data Security and Breach Notifications. Most new platforms offer excellent tools for managing known risks, as well as notifying the organization of potential malicious anomalies. However, they do not provide tools that can identify the approved application code that contains vulnerabilities. By the time the system can determine the breach or issue, it is too late.
Potential Network Security Breach
In the modern workplace, most users work both in the office as well as remote. Allowing citizen developers access to modify applications on the unknown or public network increases the potential risk of data exposure, exfiltration, and breach.
Non-adherence to corporate Cyber Security policies
Many corporate Cyber Security policies define how accounts, passwords, and permissions need to work. For Citizen Developers to make the customizations, their login accounts are allowed elevated access. Granting this, lets them store sensitive information such as usernames and passwords insecurely. This practice goes against most corporate policies that ensure the business is secure.
Lack of training and expertise
Generally, Citizen Developers are not trained software developers, have not had any formal training and often do not understand the fundamental building blocks of the applications they are customizing. However, these users then make changes as best they know how, by using snippets of code found online, hacking things together or trying it until it works. Normal formal processes do not apply because the outcome is to make it work without any of the worries or concerns when performing a standard software deployment.
What kind of malicious code do we mean?
Common JavaScript code can have a significant impact on any application. Using the following function as an example, you can see that it doesn’t do anything dangerous or malicious but could do if not validated.
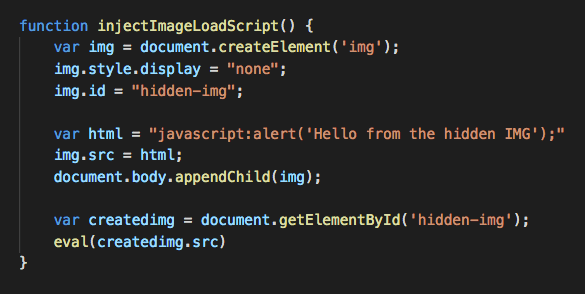
The code itself is not doing anything malicious, however, due to the nature of JavaScript coding it is injecting an item into the “Document Object Model (DOM).” The code injects a new “Image” directly at load time. The “IMG” tag loads with an arbitrary JavaScript command. The newly added “IMG” tag uses a common JavaScript “Eval()” function, ensures that the hidden code executes. The script is an easy example of how if unchecked, could lead to data exposure or vulnerability.
What mitigations can be put in place to limit the risks?
To mitigate against such attacks or mistakes; organizations must implement processes for checking and deployment. Citizen Developers need to understand that IT and Security departments have the final say in implementation and modification of cloud services. Just because it is easy and faster for them to make the changes does not negate the need for checks and balances. Citizen Developers, also need to be trained on best practices, not only for customizations but security and controls. Teaching them to follow cybersecurity standards will help to remove potential issues before it is too late.
IT and Security departments also need to perform regular cyber threat assessments that include these types of customizations. Often these are left out as the risk only applies to the overall cloud service and not the specific function or customized application.
Cloud providers often offer great Security tools, but only those that monitor and notify standard attack vectors. Most protections cover compromised accounts, data exfiltration, data deletion, data spillage, password attacking, phishing and elevation of privilege. Providing a service that can scan customizations such as scripts would be complicated to implement, potentially then limiting rapid development and possibly make the platform less appealing to organizations. Until providers can offer a service such as this, a manual process will be required.
Follow these steps to ensure customizations are secure or do not contain malicious code:
1. Identify Customizations and Locations
2. Categorize the customization by potential risk – defined by its end-user function
3. Review customized code or script
4. Perform internet searches for the same functions and scripts
a. Validate the copied code matches the online code
b. Check if these functions or scripts have known vulnerabilities
5. Check for any linked resources, such as those loaded from a Content Delivery Network (CDN)
a. Download these assets and ensure of original and not modified
b. Check if these assets have known vulnerabilities
6. Review modified assets, such as images, HTML and styles
7. Utilize open source frameworks to scan the assets, using tools such as tslint, eslint, etc.
8. Security scan the code using 3rd party tools
Utilize a Risk Assessment
Rencore’s free SharePoint Application Risk Assessment gives organizations a chance to understand how solutions added to by developers, power users or citizen developers are impacting on security. Keeping track of all applications will maximize organization productivity and keep data secure. Try our Risk Assessment for free today.





