In the previous article, I talked about Shadow IT and how important a cloud governance strategy is to keep Shadow IT within your organization in check. I talked about roles & responsibilities, sensitive information types, information protection policies, and new features & updates.
For the second part, I want to focus more on the security aspect with a cloud governance strategy for Microsoft Teams. We focus on the following topics:
- App Policy
- Authentication & authorization
- Microsoft Defender for Cloud Apps
App policy
Due to past shortcomings of Microsoft 365, other companies emerged and launched successful apps such as Dropbox, Slack, and Trello. In my opinion, Microsoft stepped up its game and made certain external apps irrelevant. The improvements for certain Microsoft 365 services reduced Shadow IT. That said, there are plenty of organizations still using external apps. Instead of shunning these apps, Microsoft offers an integration in Microsoft Teams. This is seen in the app store:
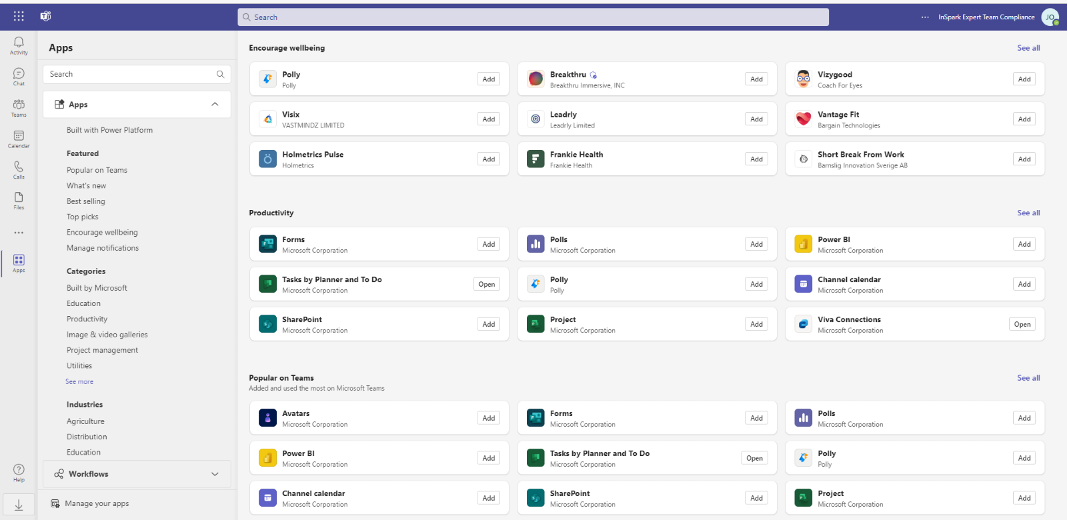
I recommend adjusting your Microsoft Teams App Policy to block all external, non-Microsoft apps. But, before you do please talk to your stakeholders. Gather an inventory of any external apps being used. If these apps can’t be replaced by Microsoft 365, you adjust the Global App Policy and block all custom apps. 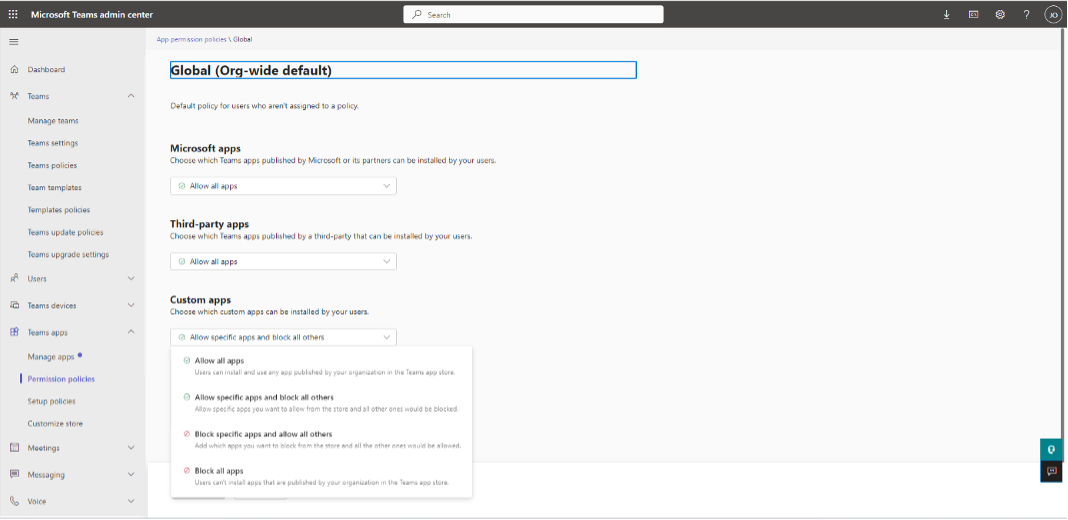
In a custom policy, you allow external apps for employees who need to use the app. The next step is reviewing the user request feature for external apps. Click here to learn more.
Authentication
Authentication is the process of verifying the identity of an employee or guest. The days of only logging in with a username and password are way behind us. Securing identities is an integral part of any cloud governance strategy. Microsoft provides the following features:
- Multi-factor authentication
- Conditional Access
- Entra Identity Protection
- Device Management
Multi-Factor Authentication (MFA)
MFA is a process in which employees or guests are prompted during the sign-in process for an additional form of identification. This is often done with a verification code on the mobile Authenticator App. MFA should be a no-brainer. You significantly reduce unauthorized access to your Microsoft 365 environment. Unfortunately, I still encounter organizations that don’t require MFA for their guests. Click here to learn more about setting up MFA for Microsoft 365.
Conditional Access (CA)
CA allows access, for employees and guests, by using signals. These signals vary from user or group membership, and location to devices. For example: If a guest wants to access Microsoft Teams, then they must use MFA to gain access. CA, just as MFA, should be a no-brainer. The following figure provides an overview1:
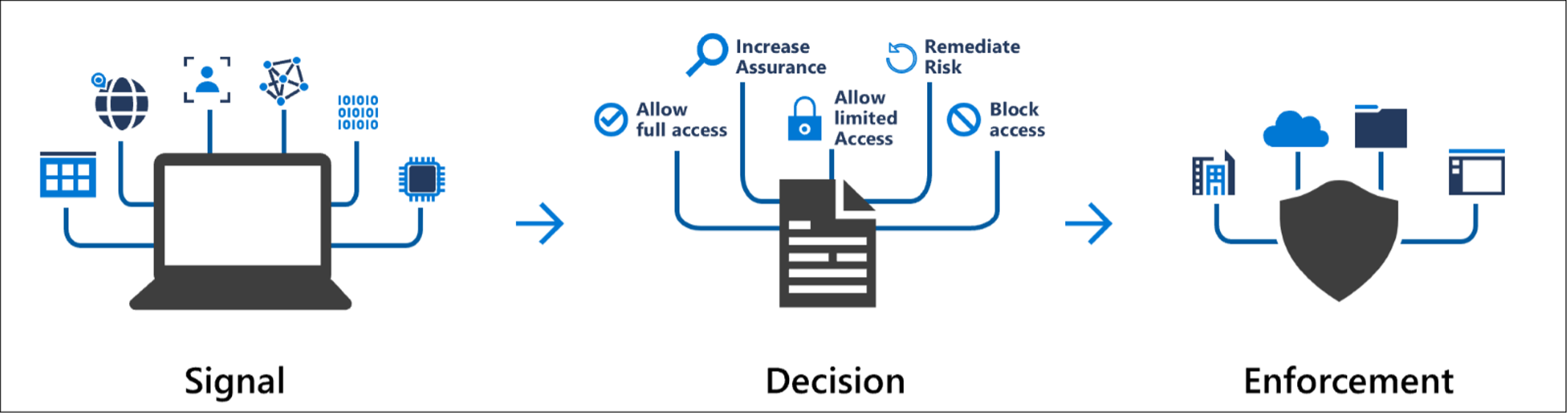
Click here to learn more about Conditional Access.
Entra Identity Protection
Entra Identity Protection helps your organization detect, investigate, and remediate identity-based risks. The service uses automated controls based on the daily learnings from signals from services such as Entra ID, Microsoft accounts and even Xbox. The following figure provides an overview2:
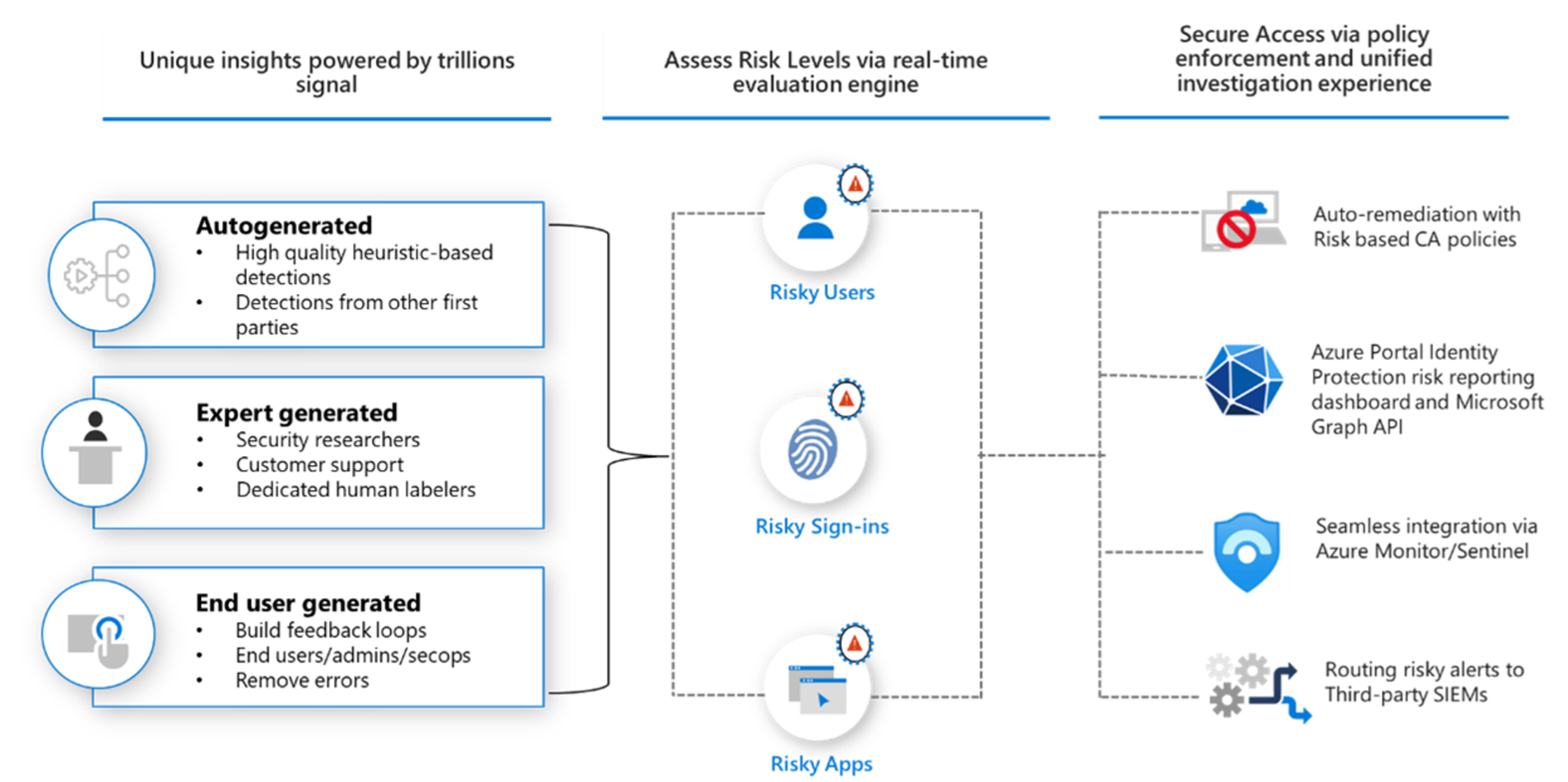
To fully benefit, you need an Azure AD Premium P2 license. Click here to learn more about Entra Identity Protection.
Device Management
Most employees, and guests, access your Microsoft 365 environment with multiple devices. Basically a laptop, and mobile phone. This is where Device Management comes into place, enabling organizations to administer and maintain devices. It helps ensure that devices are secure, up-to-date, and compliant with your organizational policies. The following figure provides an overview3:
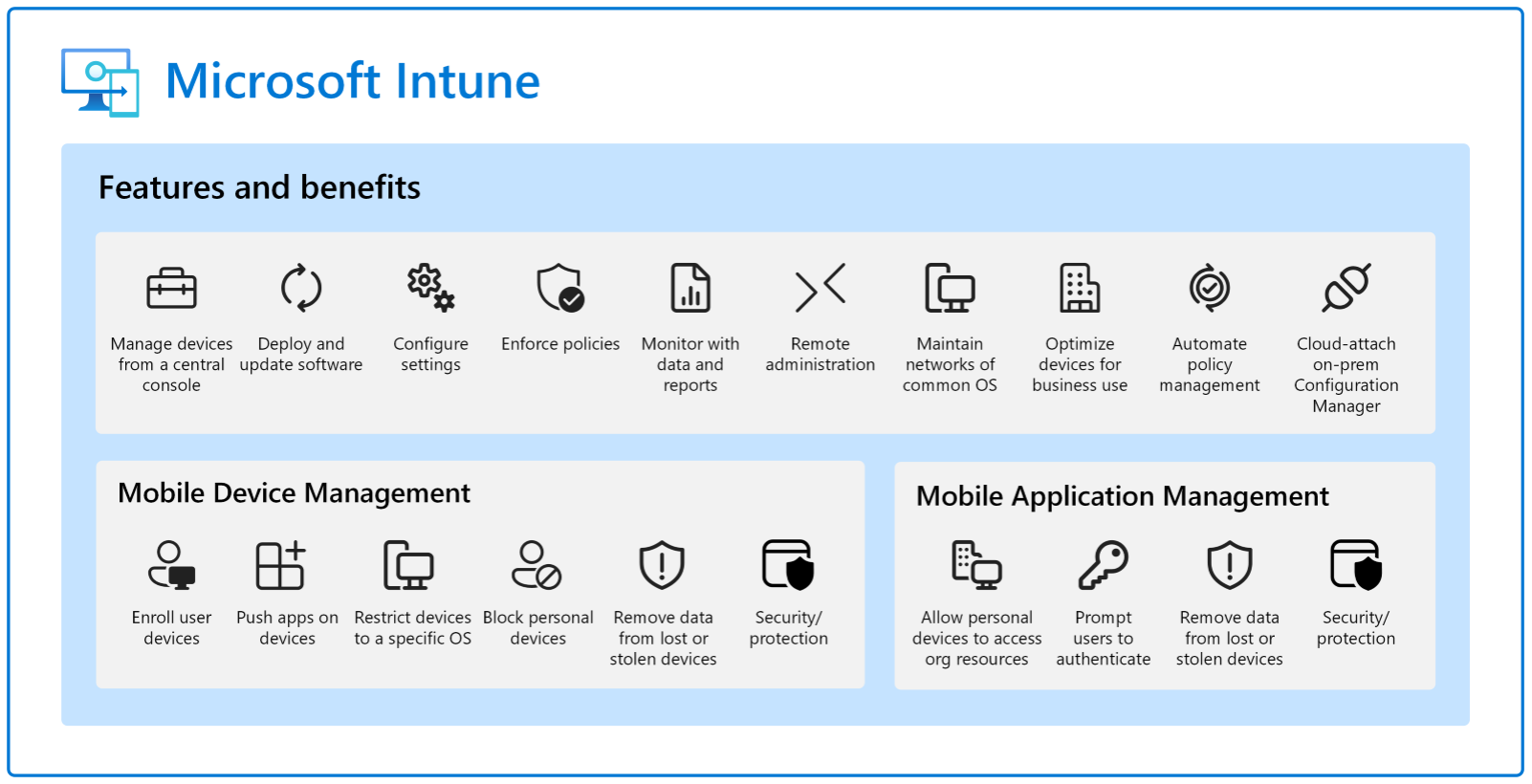
Click here to learn more about DM.
Authorization
Authorization is the process of determining whether an employee or guest has the necessary permissions to perform a specific action or access a particular resource in Microsoft Teams. The following components should be part of your cloud governance strategy:
- Privacy options
- Type & manage membership
- Guest review
- Sharing links review
- Ownerless groups
Privacy options
Microsoft Teams provides three privacy options for a team: Public, private, or org-wide. Your organization makes use of collaboration templates (type of teams). For example, projects or departments. For each template, you determine the default privacy option. Click here to learn more.
Type & manage membership
Microsoft Teams membership is divided between owners, members, and guests. You determine, for each template, the available actions. For example, members can create and delete a channel but they can’t add an app or tab. Click here to learn more about the available actions per member.
You also determine the manner of managing owners & members per type of team. This can be done manually or dynamically. The latter is interesting for larger departments or teams. Click here to learn more about dynamic membership.
Guest review
Guests don’t need access to your Microsoft 365 environment till the end of time. I advise setting up a review process for your guests. This can be done with Entra Access Review, manually by IT within Entra ID, manually by owners, and by an external tool.
Sharing links review
Comparable to reviewing guest access, there is no need to keep sharing a file externally indefinitely. The SharePoint Site Usage page provides an overview of externally shared files. Allowing the owners to manually remove sharing links. A more efficient, and user friendly, solution would be an external tool.
Ownerless teams
The recommendation for the minimal amount of owners, per team, is at least two. This prevents ownerless teams whereby the members become frustrated due to the lack of ownership and control. Microsoft provides a policy within the Microsoft 365 Administration Center to prevent ownerless teams. A more efficient solution would be an external tool.
Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps delivers full protection for SaaS applications, helping organizations monitor and protect their cloud app data across multiple feature areas. The feature that allows your organization to discover and identify Shadow IT is called Cloud Discovery. The following figure4 shows the process to roll out Cloud Discovery within your organization:
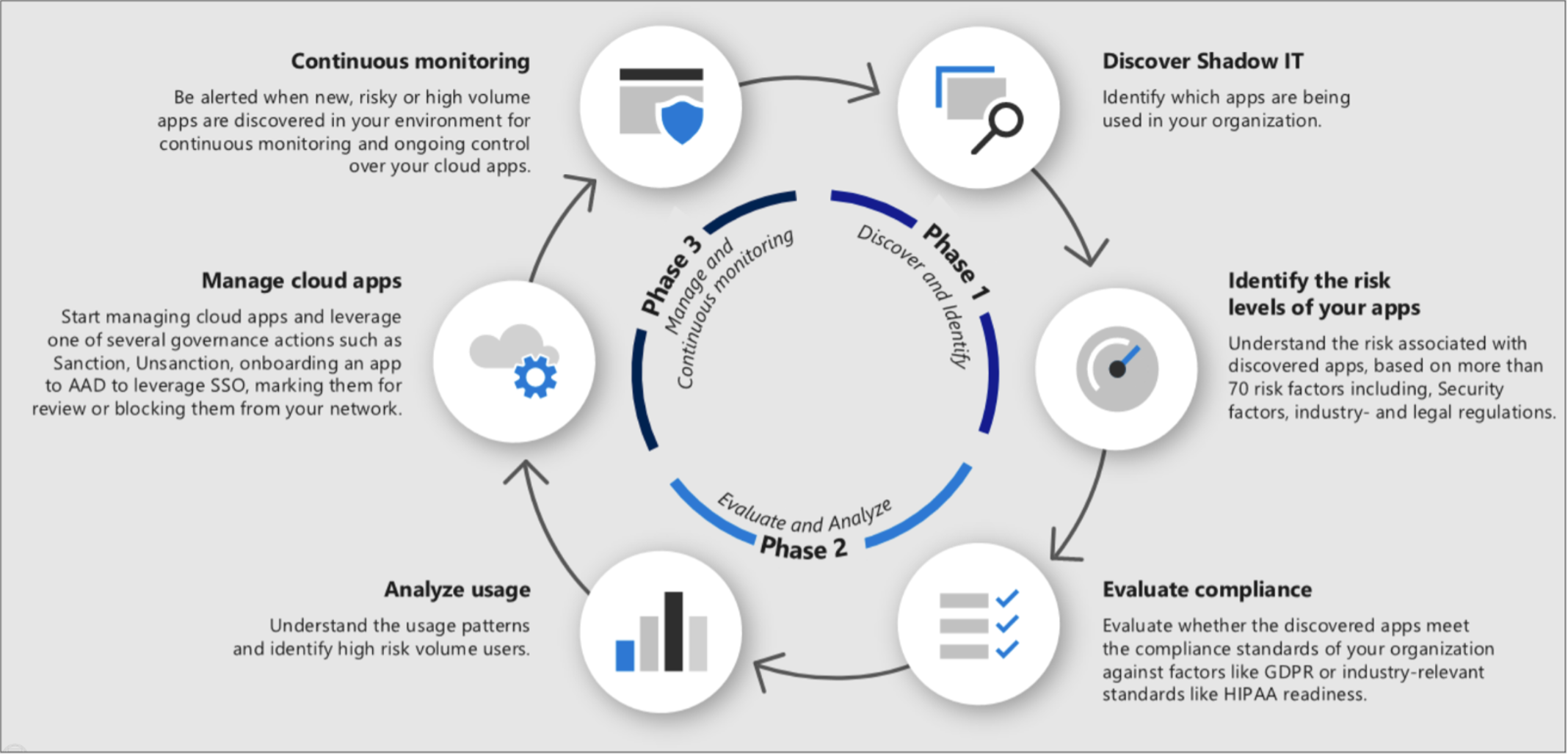
The following methods are used to discover Shadow IT within your organization:
- Integrate Cloud Discovery with Microsoft Defender for Endpoint.
- Deploy the Defender for Cloud Apps Log Collector on the firewalls and other proxies.
- Integrate Defender for Cloud Apps with your proxy.
After successfully configuring Cloud Discovery, an dashboard is available, . Pproviding your organization with valuable insights about possible Shadow IT within your organization. The following figure provides an example of the dashboard:
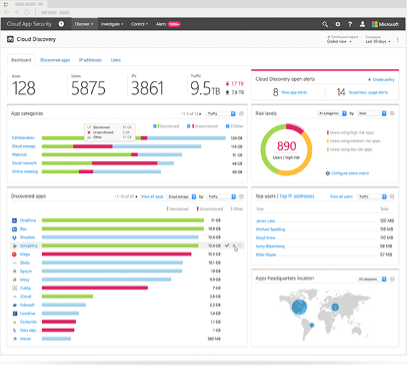
Click here to learn more about Cloud Discovery.
Conclusion
I can’t emphasize enough how important it is for your organization to proactively address shadow IT by implementing a clear governance strategy, enabling open communication with your employees, providing appropriate Microsoft 365 productivity solutions, and promoting awareness of the risks associated with Shadow IT. By doing so, your organization can minimize the negative impact of shadow IT while maintaining a secure and efficient technology landscape.
A note from Rencore
Our cloud collaboration governance tool Rencore Governance provides you with maximum flexibility and efficiency in your governance approach for Microsoft Teams. With the help of Rencore Governance, you can identify all Teams channels and sites and manage and govern user activities, access and permissions. If you haven’t already, start a free trial to know more about the tool.
If you want to know more about Microsoft Teams Governance, then download our free whitepaper titled ‘Microsoft Teams Governance Best Practices.’




