Reduce the carbon footprint of Microsoft 365
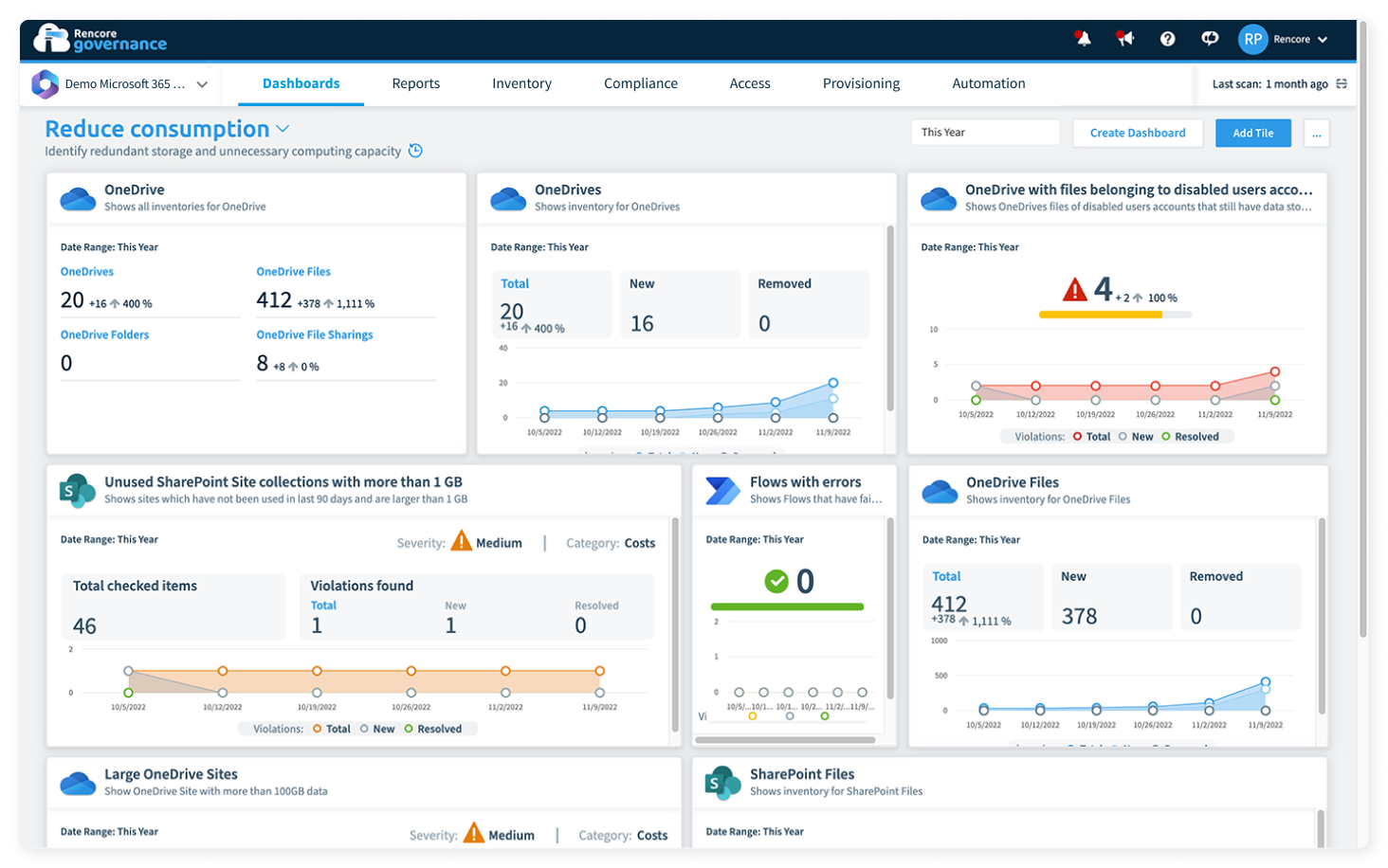
Our tool Rencore Governance provides you with full visibility into the carbon footprint of our Microsoft 365. Once connected to your tenant, Rencore Governance identifies Microsoft 365 services and workloads responsible for excess storage and computing power use. Increase your company’s sustainability by using Rencore’s powerful checks and automations to reduce the energy consumption of your IT significantly!
All your cloud services insights in one central place
De-duplicate data
Microsoft 365 makes it easy to collaborate and share data. However, multiple storage locations inevitably lead to duplicate data. Identify duplicates, remove unnecessary versions, reduce the energy required for your IT storage and reduce your carbon footprint by approx. 420 grams CO2 per KWh saved.
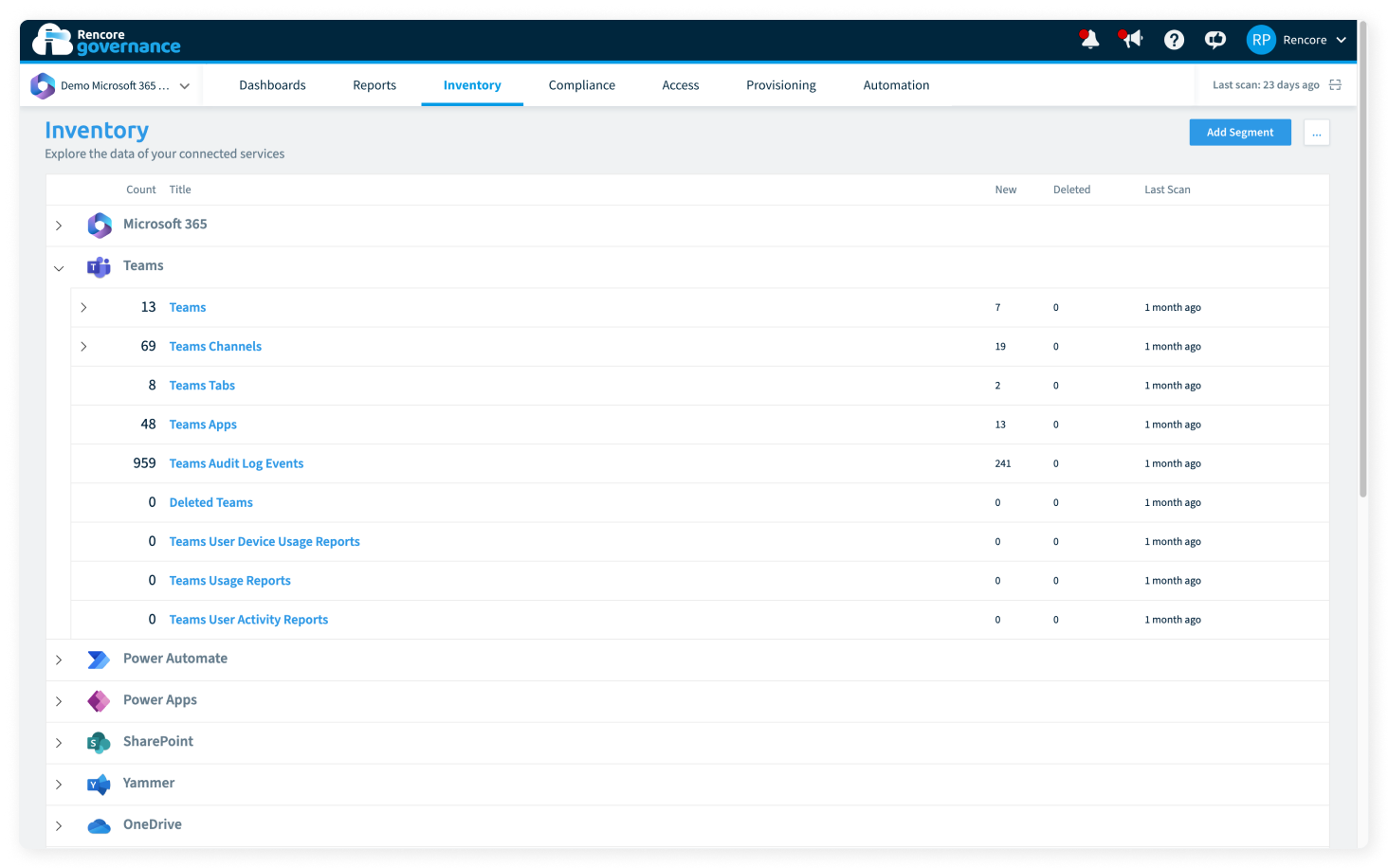
Reduce computing consumption
IT processes heavily rely on computing power. And although Microsoft pledges to become Carbon negative by 2030, getting rid of unnecessary Azure consumption today is something that will positively affect both your budget and your carbon footprint.
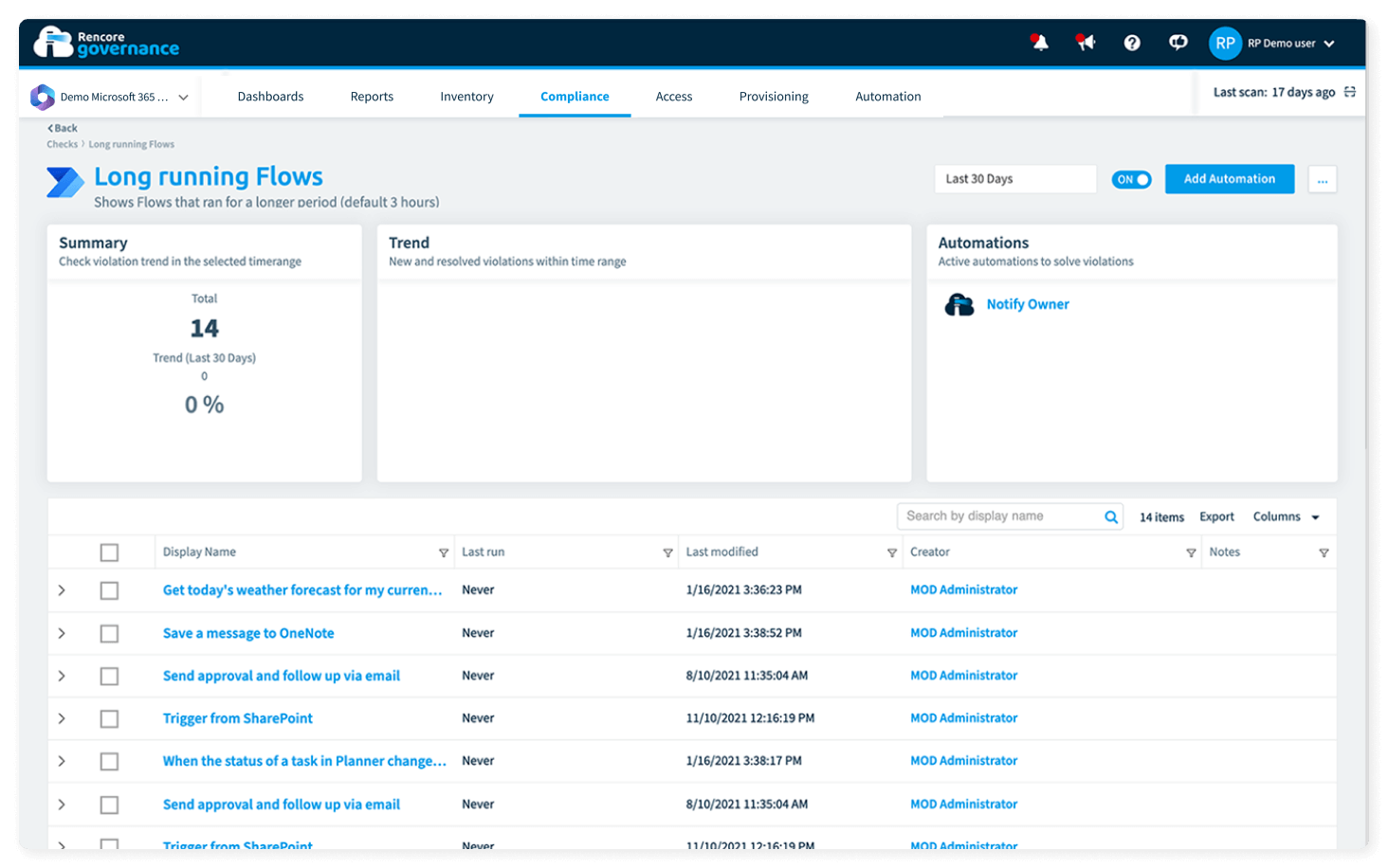
Crack down on data transfer
Cloud computing has massive environmental benefits over on-premises data centers. However, one thing the cloud promotes is data transfer. Rencore Governance allows you to identify large amounts of data that are shared externally and helps you reduce unnecessary or outdated access to decrease data transfer by approx. 140 grams CO2 per Gigabyte.
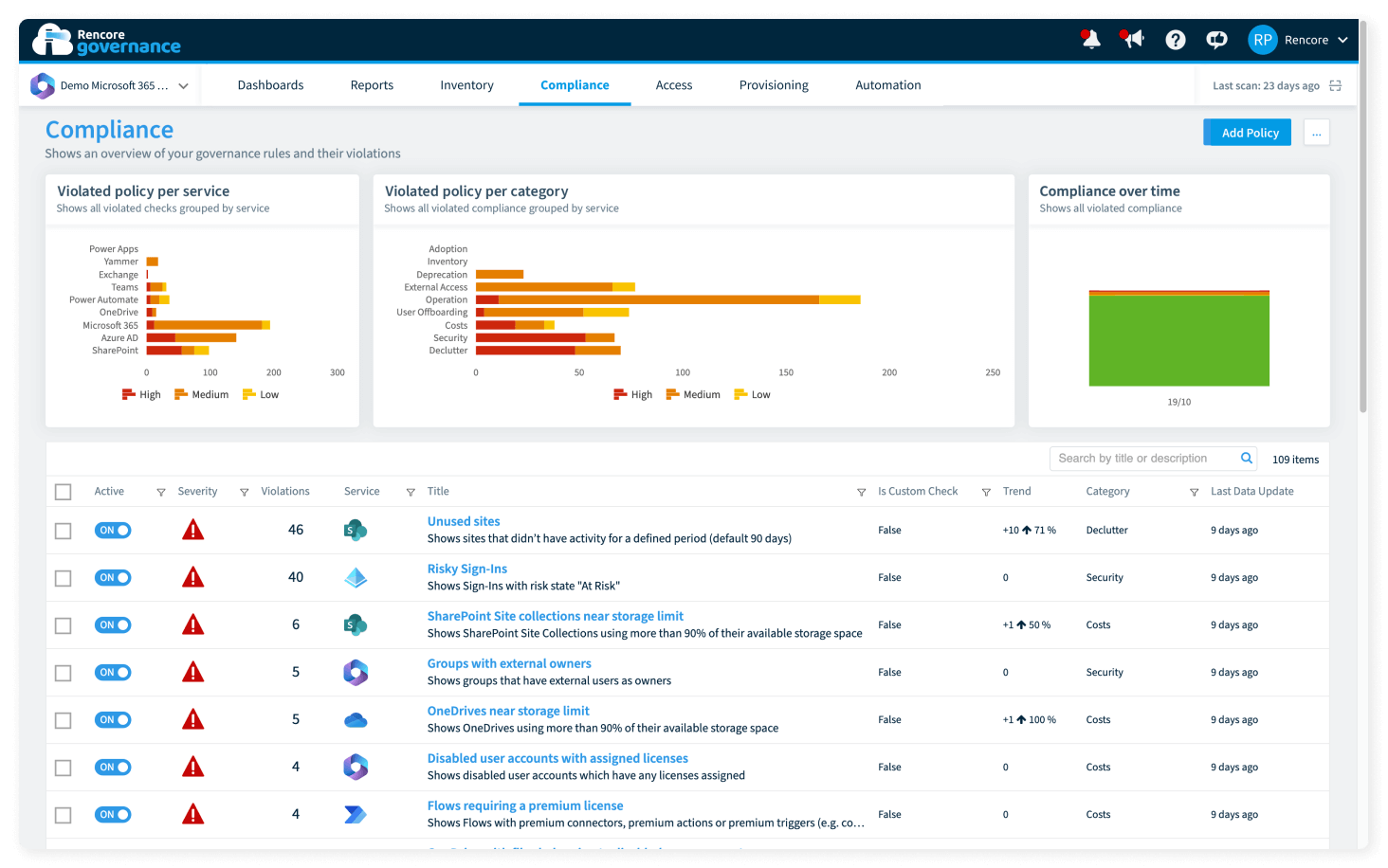

Reduce your IT’s carbon footprint today!
Software built in Germany
Built to the highest engineering standards and loved by Microsoft 365 admins, enterprise architects, and IT security professionals across the globe.
Secure Microsoft Azure hosting
Rencore Governance runs in Microsoft Azure, meeting international security requirements and certifications (Azure CIS, PCI DSS, SOC TSP, ISO 27001).
Certified to the highest standards
Our platform is fully SOC 2 Type 2 accredited and GDPR-compliant to help you meet internal and external audit requirements with confidence.